Breaking Pwn Adventure 3 - Part 2(Speed Hack, SuperJump and Pointers Offline Mode)
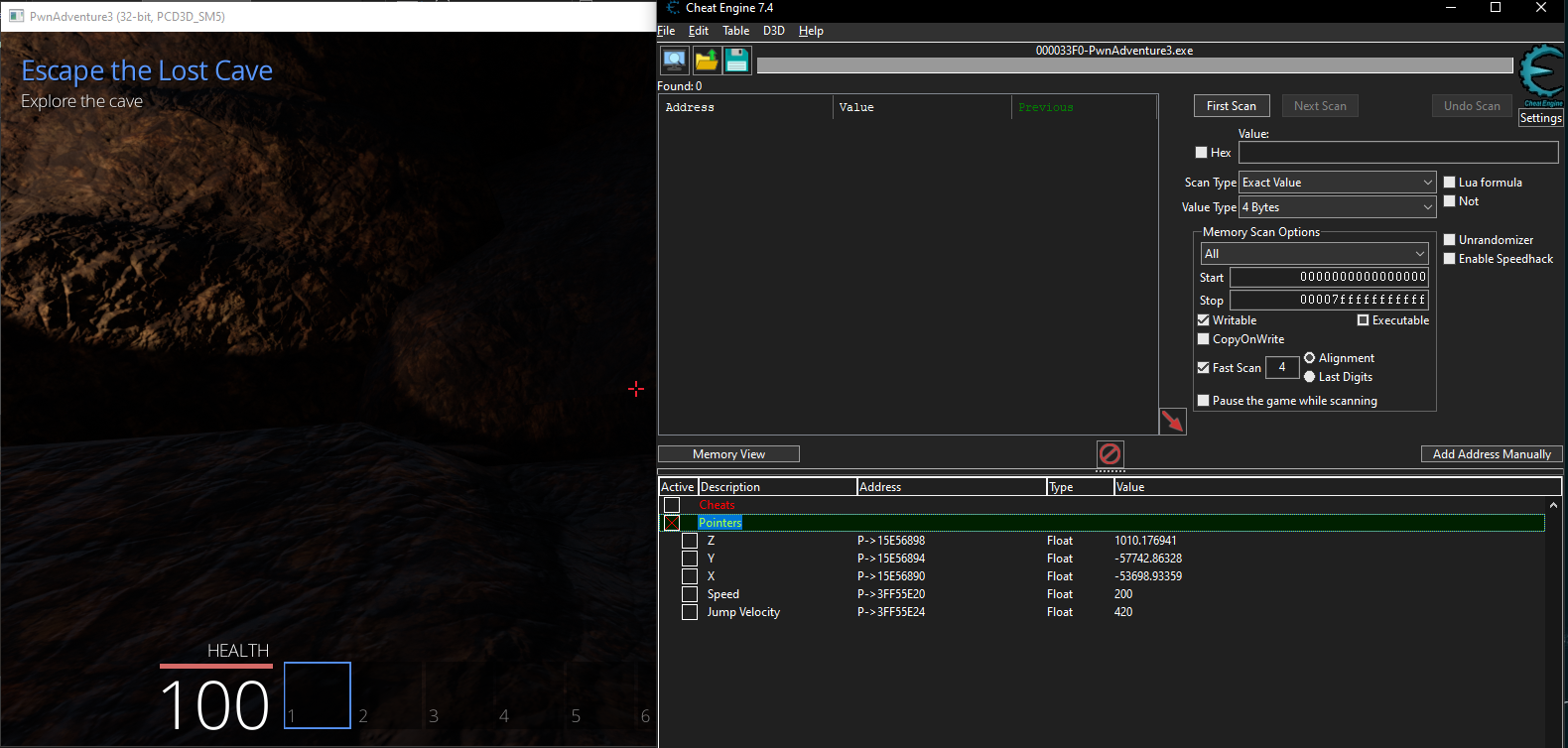

 Creating God Mode and One Hit Kills on Pwn Adventure 3 using Cheat Engine
Creating God Mode and One Hit Kills on Pwn Adventure 3 using Cheat Engine

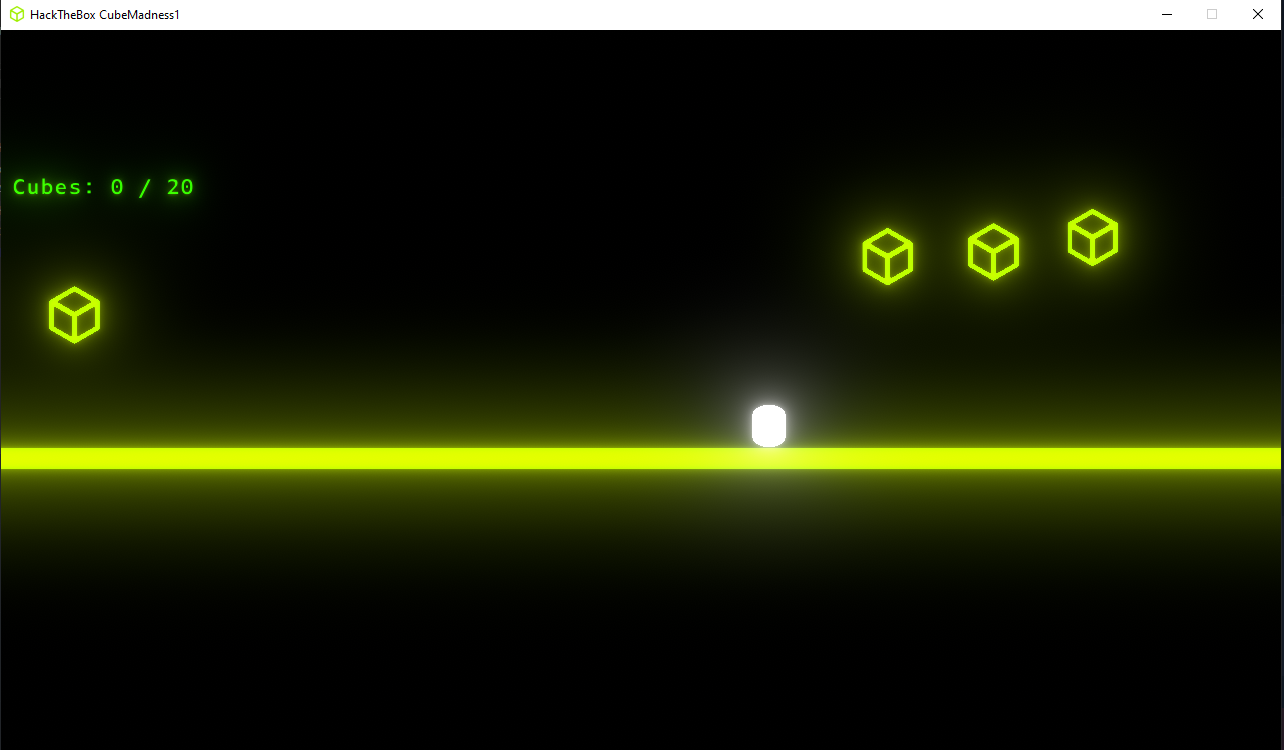 This is the walkthrough for the newly introduced challenge category GamePWN on HackTheBox
This is the walkthrough for the newly introduced challenge category GamePWN on HackTheBox
 Ra is a windows machine which starts with a typical business website for Windcorp where there is a password reset function which can be used to change a user’s password to gain access to a SMB share to download spark live chat application which is vulnerable that can be used to harvest a user’s NTLM hash that can be used to gain initial access to the machine.On further exploring the machine a script can be seen that contains a username who’s password can be changed since the user has extended rights to change password as he is a member of the account operator group.Analysing the script we can see that there is command injection vulnerability that can be abused to gain admin privilege and pwn the machine
Ra is a windows machine which starts with a typical business website for Windcorp where there is a password reset function which can be used to change a user’s password to gain access to a SMB share to download spark live chat application which is vulnerable that can be used to harvest a user’s NTLM hash that can be used to gain initial access to the machine.On further exploring the machine a script can be seen that contains a username who’s password can be changed since the user has extended rights to change password as he is a member of the account operator group.Analysing the script we can see that there is command injection vulnerability that can be abused to gain admin privilege and pwn the machine
 Here is a short write-up on an interesting bug that I found while testing a site where I was able to chain multiple IDORs to execute Code on the server
Here is a short write-up on an interesting bug that I found while testing a site where I was able to chain multiple IDORs to execute Code on the server
 This is the walkthrough for the challenges that were provided as a part of COCON’s DomeCTF
This is the walkthrough for the challenges that were provided as a part of COCON’s DomeCTF
 This is the walkthrough for the challenges that were provided as a part of Sector443’s CTF
This is the walkthrough for the challenges that were provided as a part of Sector443’s CTF

 Creating God Mode and One Hit Kills on Pwn Adventure 3 using Cheat Engine
Creating God Mode and One Hit Kills on Pwn Adventure 3 using Cheat Engine

 This is the walkthrough for the newly introduced challenge category GamePWN on HackTheBox
This is the walkthrough for the newly introduced challenge category GamePWN on HackTheBox
 This is the walkthrough for the challenges that were provided as a part of COCON’s DomeCTF
This is the walkthrough for the challenges that were provided as a part of COCON’s DomeCTF
 This is the walkthrough for the challenges that were provided as a part of Sector443’s CTF
This is the walkthrough for the challenges that were provided as a part of Sector443’s CTF
 Here is a short write-up on an interesting bug that I found while testing a site where I was able to chain multiple IDORs to execute Code on the server
Here is a short write-up on an interesting bug that I found while testing a site where I was able to chain multiple IDORs to execute Code on the server
 Ra is a windows machine which starts with a typical business website for Windcorp where there is a password reset function which can be used to change a user’s password to gain access to a SMB share to download spark live chat application which is vulnerable that can be used to harvest a user’s NTLM hash that can be used to gain initial access to the machine.On further exploring the machine a script can be seen that contains a username who’s password can be changed since the user has extended rights to change password as he is a member of the account operator group.Analysing the script we can see that there is command injection vulnerability that can be abused to gain admin privilege and pwn the machine
Ra is a windows machine which starts with a typical business website for Windcorp where there is a password reset function which can be used to change a user’s password to gain access to a SMB share to download spark live chat application which is vulnerable that can be used to harvest a user’s NTLM hash that can be used to gain initial access to the machine.On further exploring the machine a script can be seen that contains a username who’s password can be changed since the user has extended rights to change password as he is a member of the account operator group.Analysing the script we can see that there is command injection vulnerability that can be abused to gain admin privilege and pwn the machine
 In this post, I reverse engineer a real-world Android malware campaign targeting SBI bank customers, uncovering how attackers use APK droppers to deploy SMS-hijacking trojans.
In this post, I reverse engineer a real-world Android malware campaign targeting SBI bank customers, uncovering how attackers use APK droppers to deploy SMS-hijacking trojans.
 In this post, I reverse engineer a real-world Android malware campaign targeting SBI bank customers, uncovering how attackers use APK droppers to deploy SMS-hijacking trojans.
In this post, I reverse engineer a real-world Android malware campaign targeting SBI bank customers, uncovering how attackers use APK droppers to deploy SMS-hijacking trojans.