Breaking Pwn Adventure 3 - Part 2(Speed Hack, SuperJump and Pointers Offline Mode)
In this part I will be explaining how to increase out player speed and our jump velocity and finding pointers to these values to be persistant.
Speed Hack & Super Jump
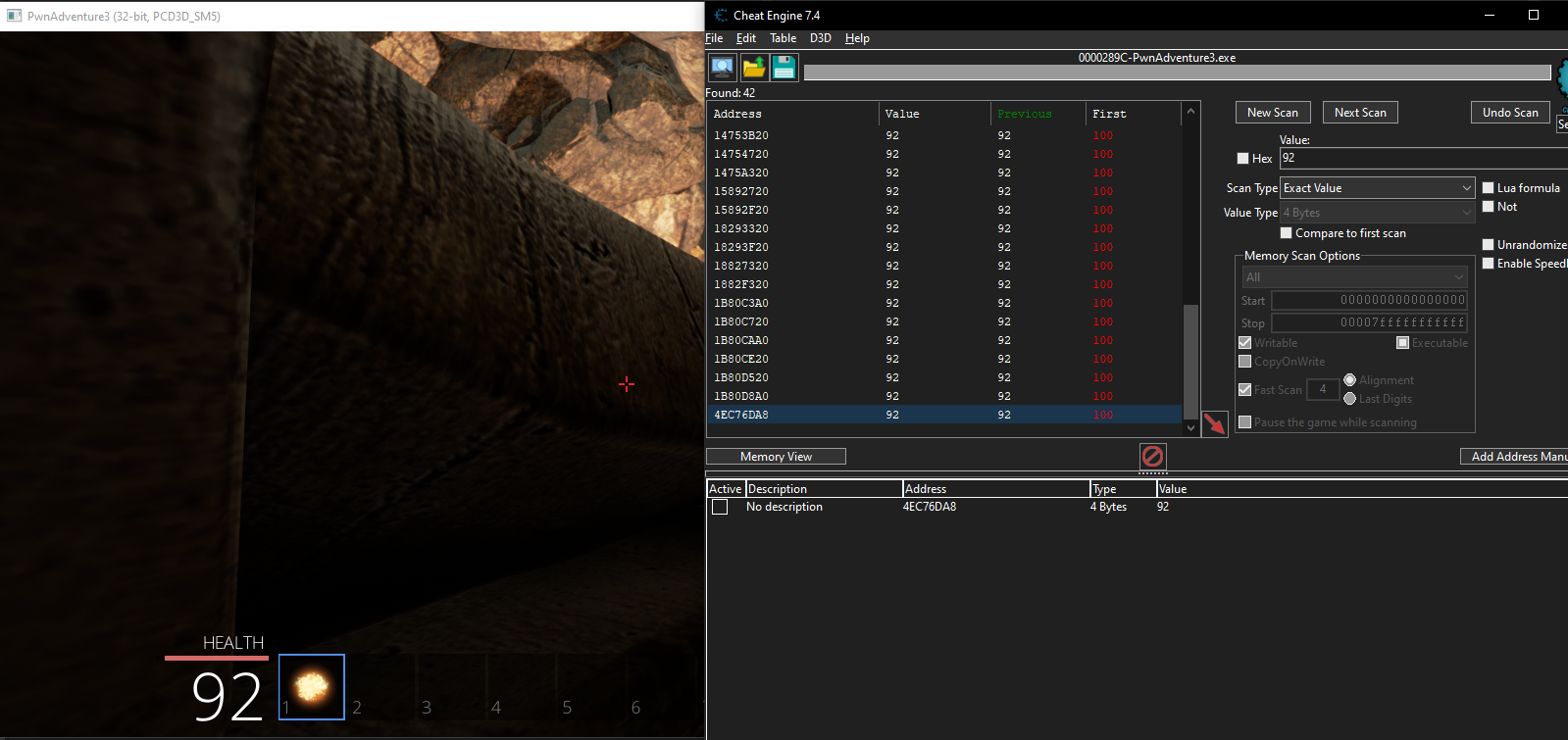
We can start by attaching our game to cheat engine and scaning for the health value of the player.
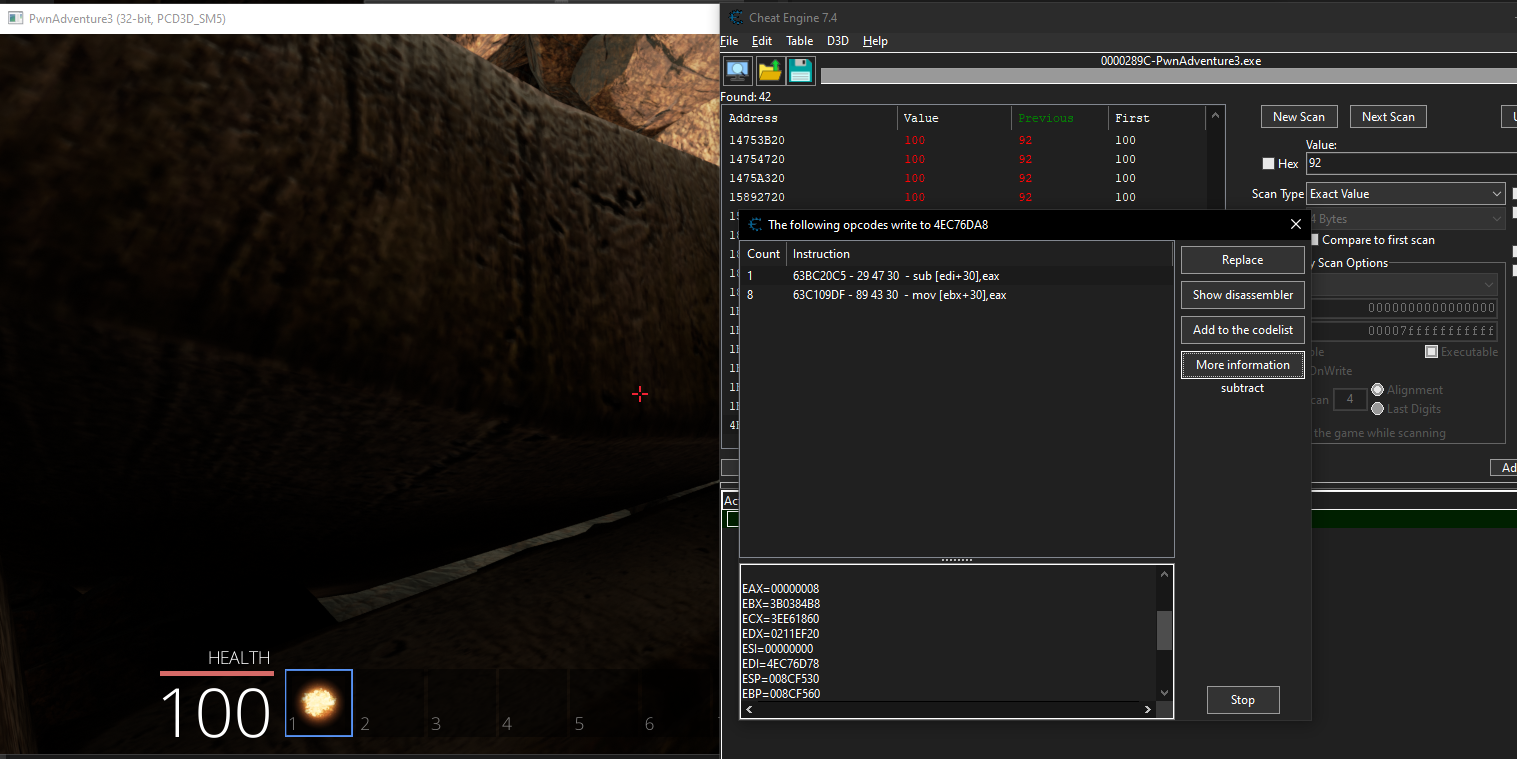

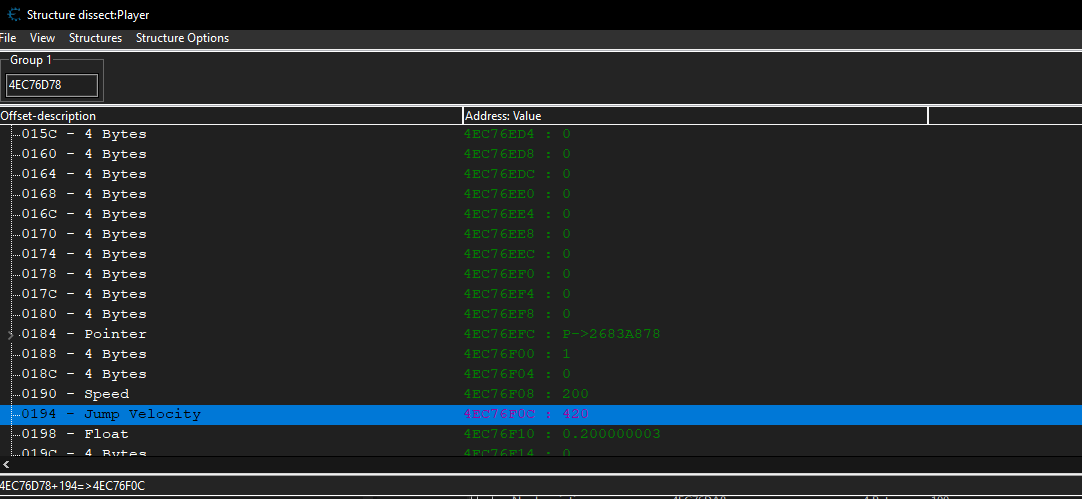
During Dissect Data Structure the base address should be used
Now we can add our players base address in the box labeled Group 1 and then click on structures and then Define a new structure.
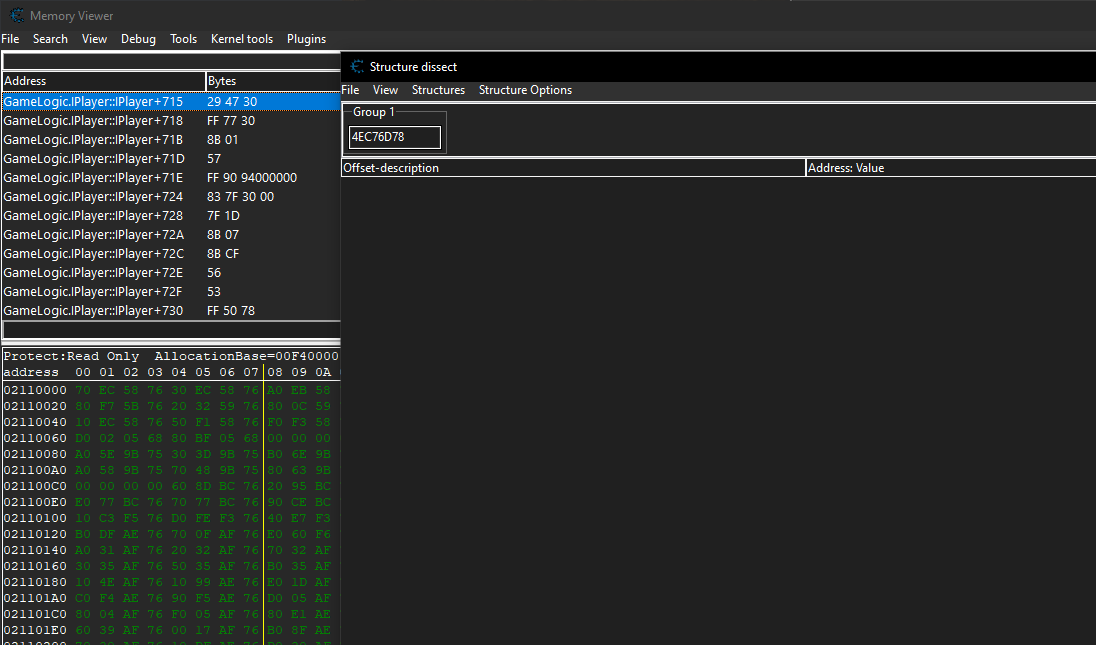
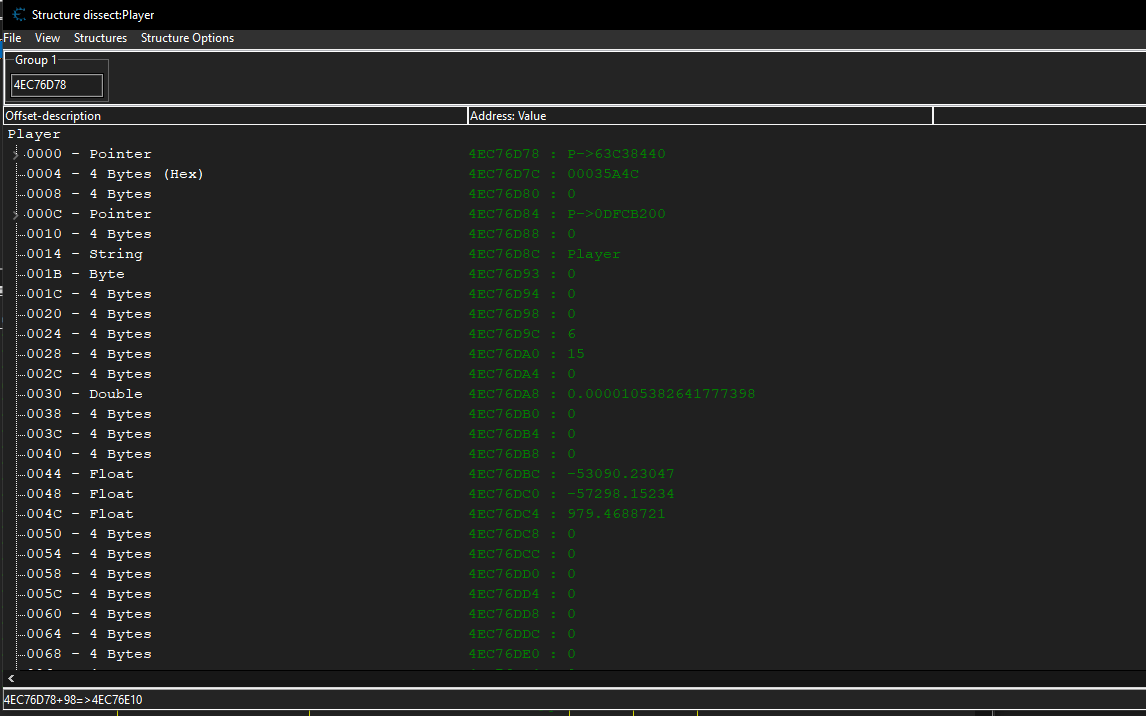
This is not an efficent method as there are chances for our game to crash if we change a wrong structure value.
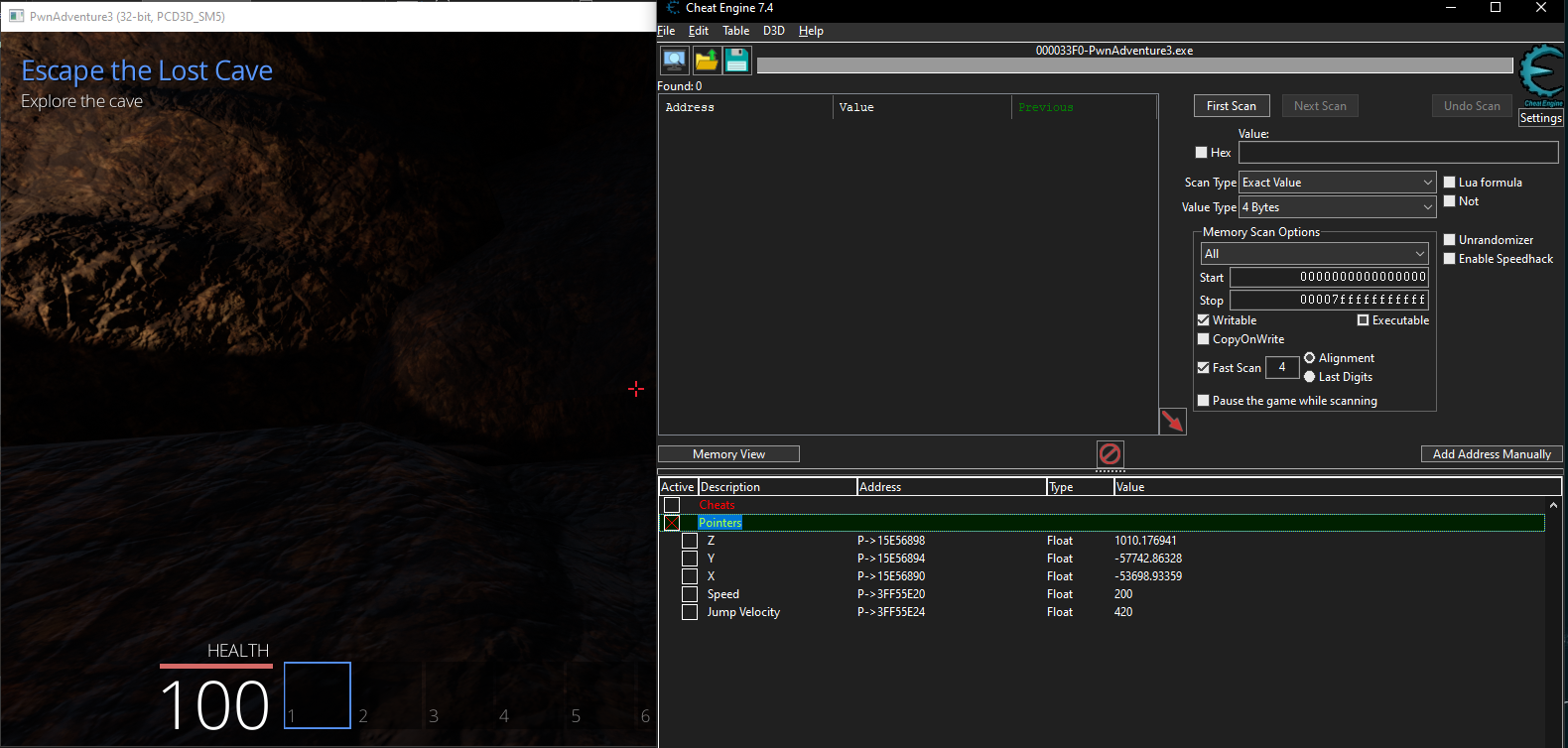
At offset 190 there is a value of 200 we can add it to our address list and change it to a higher value and try moving in game.
As we can see our player’s movement speed increased and we are zooming across the map.
For superjump we use the same method to find the offset where our jump velocity is stored in this game its stored right next to the player’s speed at offset 194 the default value is set to 420.Lets change it to a higher amount and try to jump.
Changing it to a higher value has made our player to jump much higher but there is one issue unlike the Gode Mode hack that was made in previous part this is not persistant which means that if we close the game this memory address will become invalid due to ASLR thats where pointers come in rescue.
Pointers
Due to ASLR when a game restarts the previous addresses that were used will become invalid in order for the game to find the correct address pointers are used some games use single level pointers which means only one offset will be present. Some games use multilevel pointers where there might be 5 or 6 levels of offsets. Guided hacking and LiveOverflow has made an incredible set of videos that tells about pointers and why this is used in development.
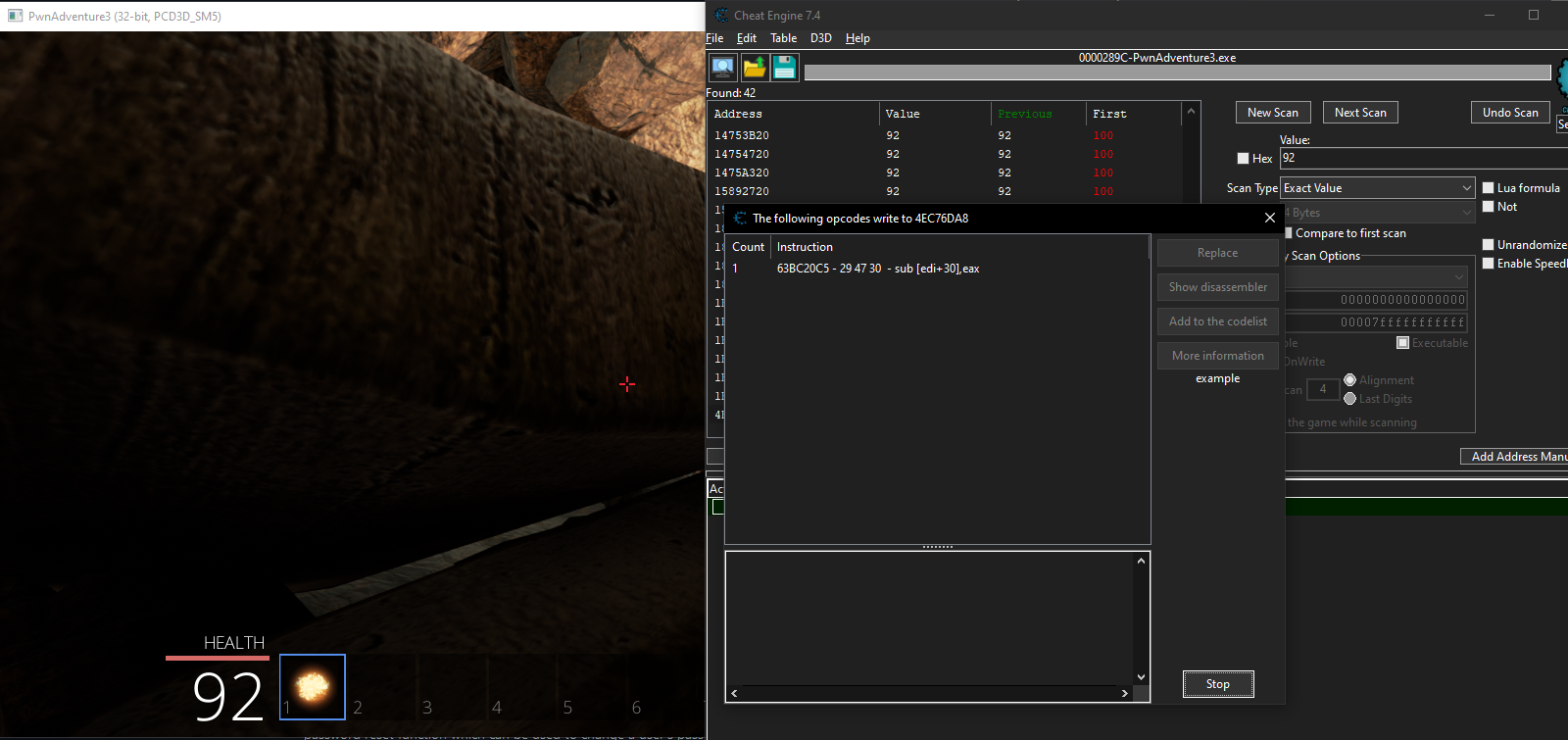
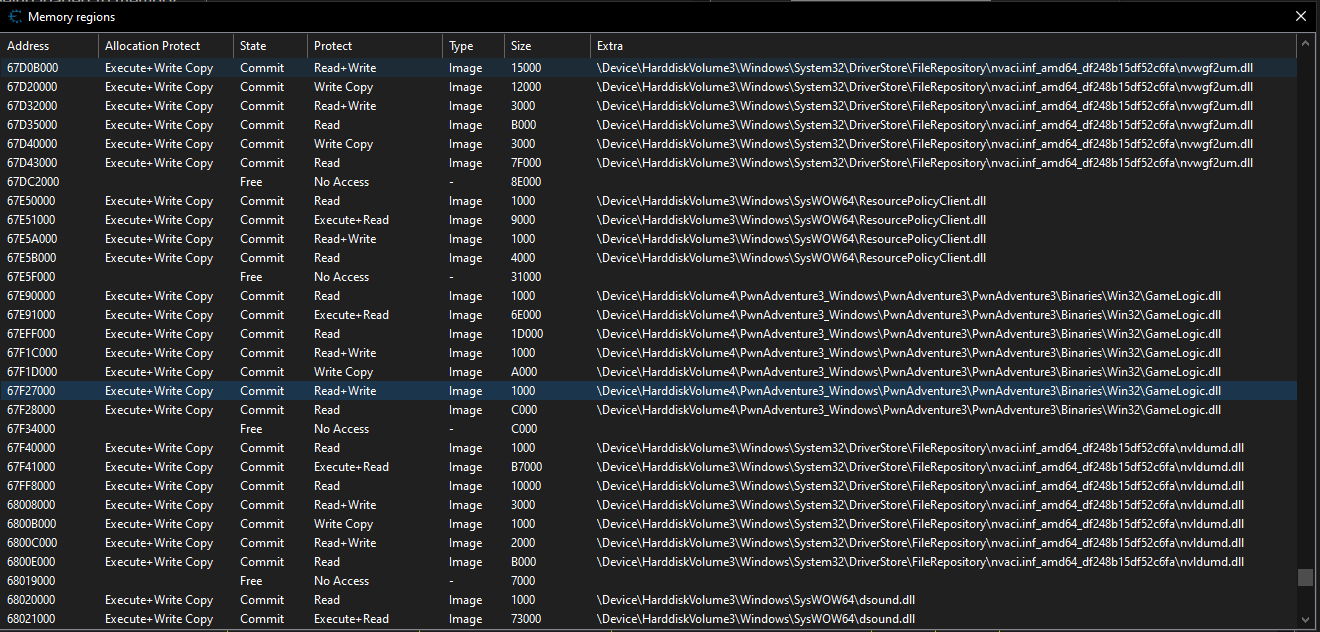
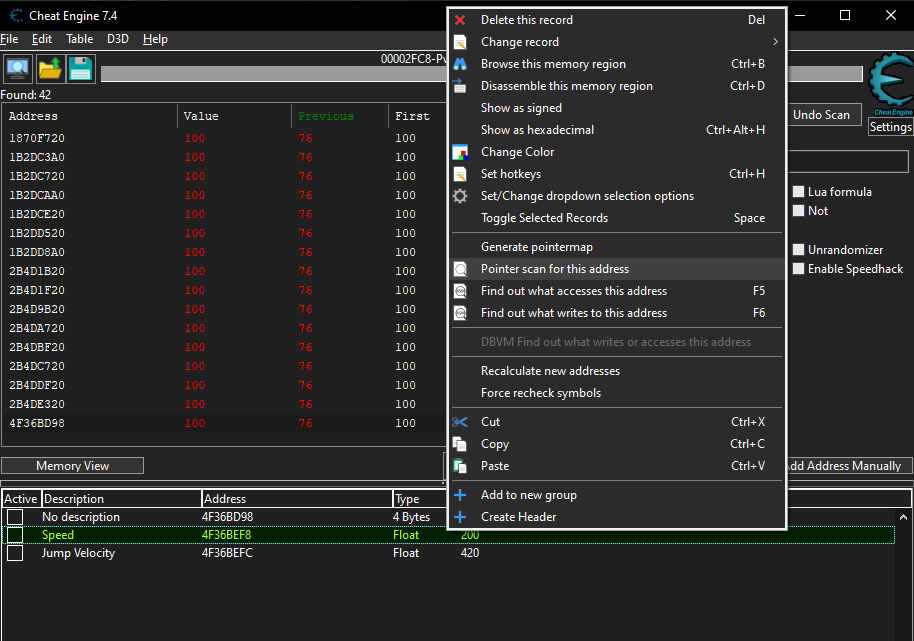
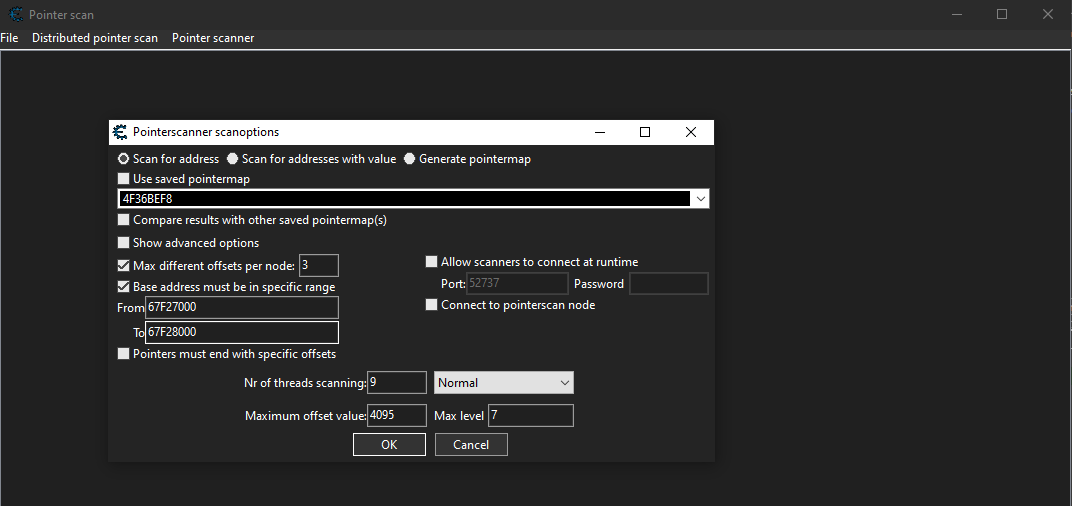
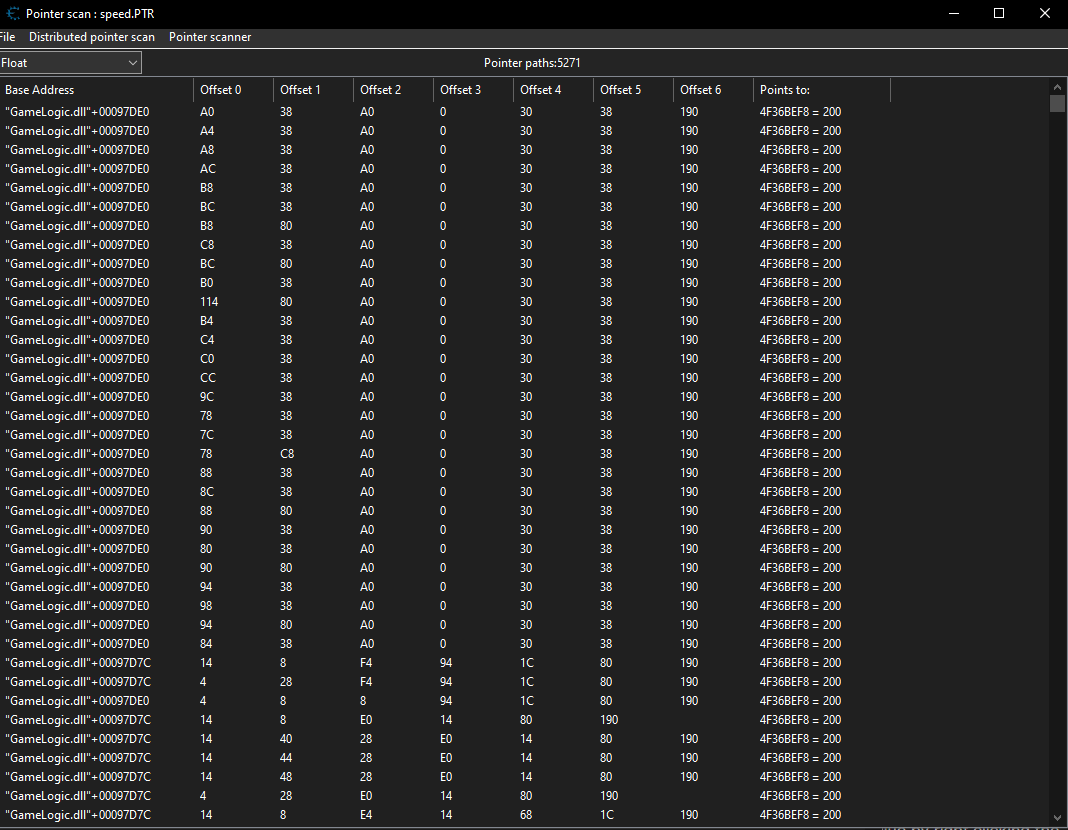
We can now start by doing a pointer scan on the player’s speed value by right clicking the value and selecting pointer scan for this address and continue which will give out a list of pointers that points to our player speed address normally we can use this method but for this game even though we get pointers that will be invalid when we restart the game since all the logic is tied to the GameLogic.dll file for that we need to find the starting and ending address of the DLL and restrict our pointer scan within that address space for that we can go to the dissassembler and click on view then Memory Regions which will give a list of addresses that the game uses scrolling down we need to find the address where our GameLogic.dll is being loaded to memory.
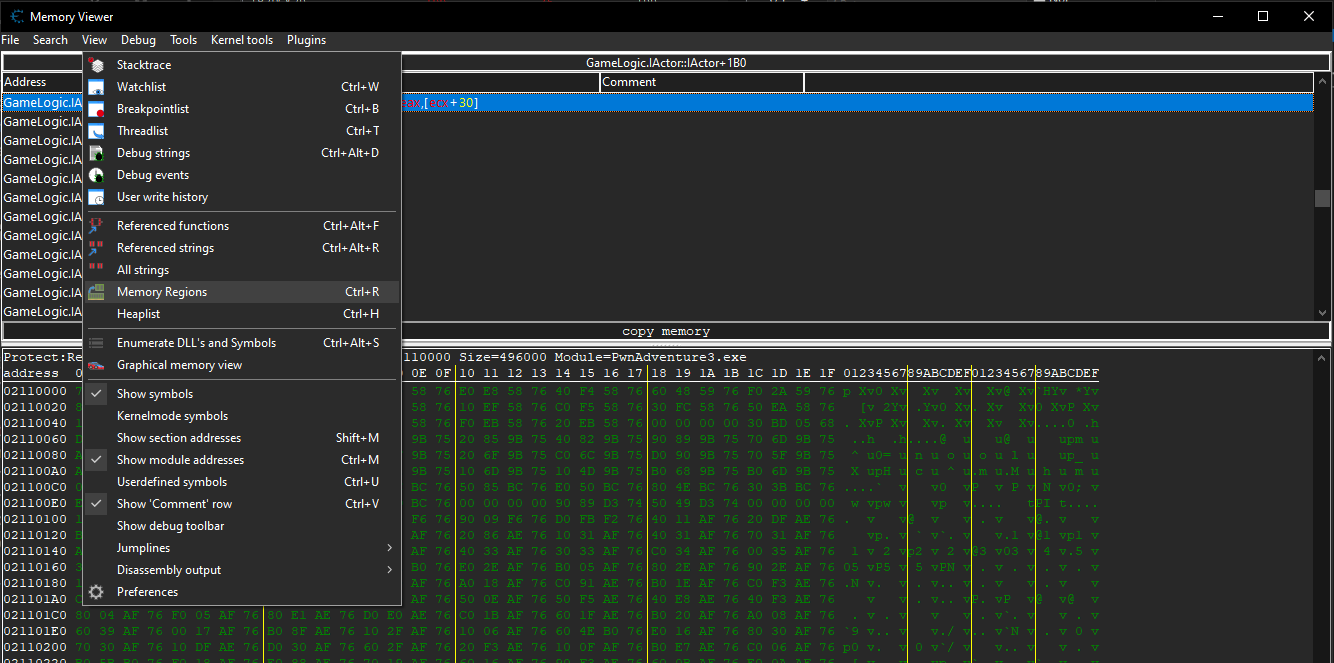
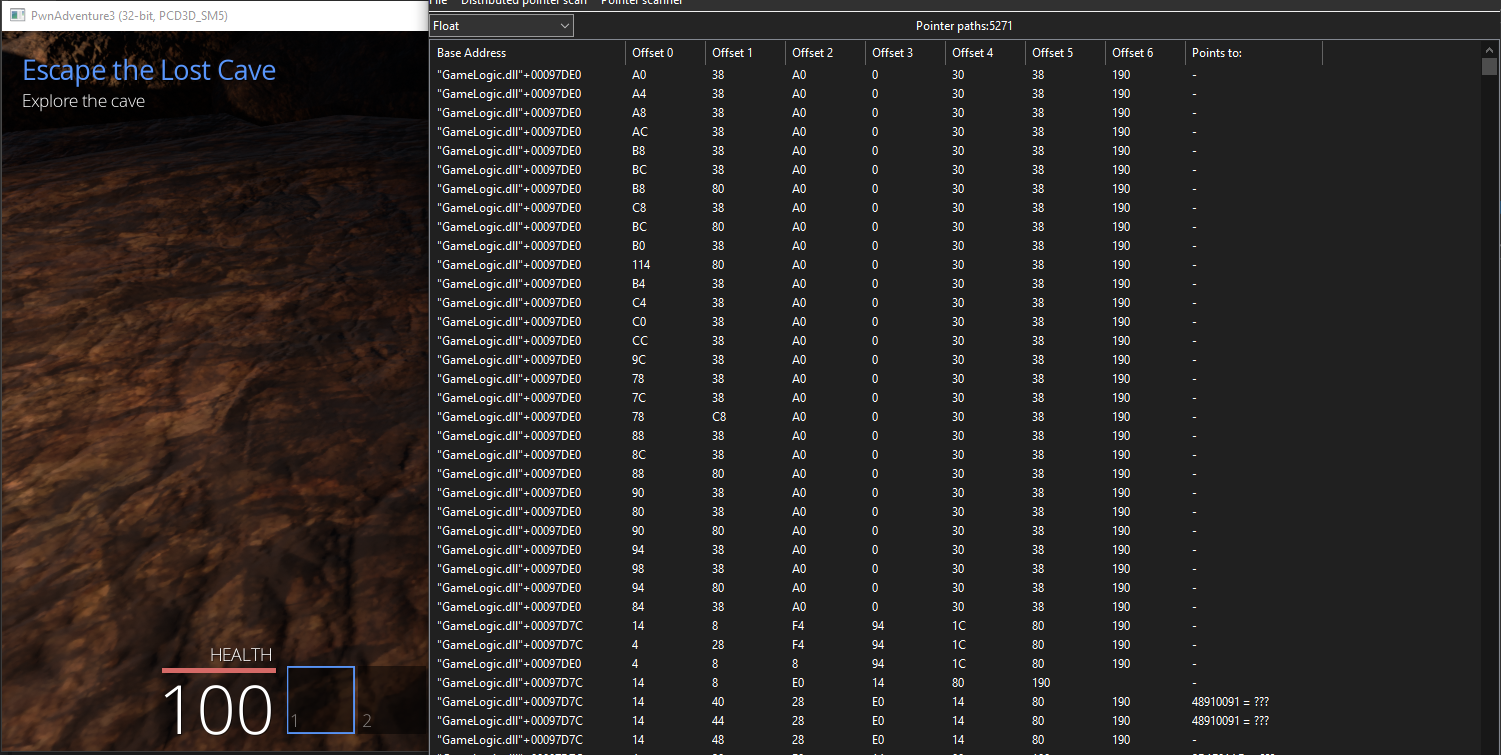
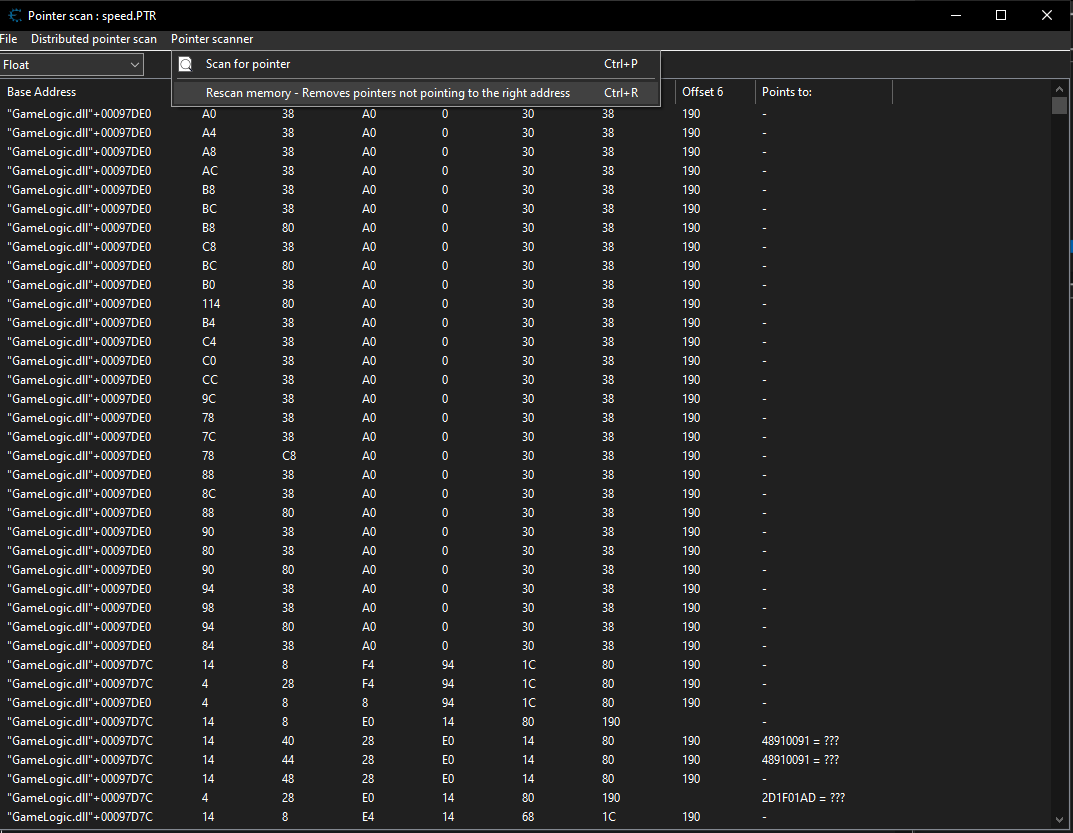
The cheat engine cheat table is available in my github if anyone wishes to try out.